我这里设备的环境有两个,一个是17.6.8a的版本;一个是15.8(3)M8的版本,两个版本都可以正常工作。
1,先处理下设备的证书。
crypto key generate rsa modulus 2048 label nj-home-rsa
#先生成一个RSA的密钥
crypto pki server ca.local
no database archive
issuer-name cn=ca.local, ou=iteachs.com
grant auto
eku server-auth client-auth
no shutdown
#配置证书服务器
ip http server
#开启http服务,不然证书服务器无法生效
crypto pki trustpoint acvpn.local
enrollment url http://192.168.50.254:80
serial-number
subject-name cn=acvpn.local, ou=iteachs.com
subject-alt-name acvpn.local
revocation-check none
rsakeypair nj-home-rsa
#创建一个个人证书点
crypto pki authenticate acvpn.local
crypto pki enroll acvpn.local
#进行证书验证和申请查看证书相关信息
#show crypto key mypubkey rsa
% Key pair was generated at: 20:59:29 Beijing Nov 17 2024
Key name: nj-home-rsa
Key type: RSA KEYS
Storage Device: private-config
Usage: General Purpose Key
Key is not exportable. Redundancy enabled.
Key Data:
30820122 300D0609 2A864886 F70D0101 01050003 82010F00 3082010A 02820101
00BA8E31 6BCD6284 06B9CA72 3B6D75CA 2135B2E6 DAC9F031 4E5DD303 9AAD91FF
0B8A6E13 5E77B9CD 597A043E 0B1B04BD 07920804 0C54A256 F6F96E24 37F2A016
BCFED0DB D1731F5D CE35B5C0 474922B2 73B0DE59 39BE5B88 1A4ED501 27A5D9B8
1A3CDBC7 3803EAEB B15C60F3 8860CD09 3BF819DB 34978237 CD131905 129BB633
0195B594 5BA2DA28 ECE15B77 A48BF73B 42ADD239 B00CE711 AA93072D 76B4BE73
31940FB6 BBE55795 AEA543E7 5C9255FF D1FC182B 44ADEE0A 14A69CDD A491E1B6
71AC0511 DA363B84 C9F1DF72 2B403AD8 947A35AA 94B49178 959E21A7 93ABB2DA
AA2D65E8 35A02602 67F27196 C25058EA 29382CA0 E7F911AE F2F64B1A BFEC7CB9
C7020301 0001
#查看RSA密钥
#show crypto pki certificates acvpn.local
Certificate
Status: Available
Certificate Serial Number (hex): 03
Certificate Usage: General Purpose
Issuer:
cn=ca.local
ou=iteachs.com
Subject:
Name: NJ-Home-C1117.iteachs.com
Serial Number: FGL2342L2UQ
serialNumber=FGL2342L2UQ+hostname=NJ-Home-C1117.iteachs.com
cn=acvpn.local
ou=iteachs.com
Validity Date:
start date: 10:18:37 Beijing Nov 21 2024
end date: 10:18:37 Beijing Nov 21 2025
Associated Trustpoints: acvpn.local
Storage: nvram:calocal#3.cer
CA Certificate
Status: Available
Certificate Serial Number (hex): 01
Certificate Usage: Signature
Issuer:
cn=ca.local
ou=iteachs.com
Subject:
cn=ca.local
ou=iteachs.com
Validity Date:
start date: 15:06:11 Beijing Nov 20 2024
end date: 15:06:11 Beijing Nov 20 2027
Associated Trustpoints: acvpn.local ca.local
Storage: nvram:calocal#1CA.cer
#查看个人证书2,处理下acvpn.xml的anyconnect profile文件,注意该文件名称必须是acvpn.xml。
<?xml version="1.0" encoding="UTF-8"?>
<AnyConnectProfile xmlns="http://schemas.xmlsoap/encoding/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://schemas.xmlsoap/encoding/ AnyConnectProfile.xsd">
<ClientInitialization>
<UseStartBeforeLogon UserControllable="true">false</UseStartBeforeLogon>
<AutomaticCertSelection UserControllable="true">false</AutomaticCertSelection>
<ShowPreConnectMessage>false</ShowPreConnectMessage>
<CertificateStore>All</CertificateStore>
<CertificateStoreMac>All</CertificateStoreMac>
<CertificateStoreOverride>false</CertificateStoreOverride>
<ProxySettings>Native</ProxySettings>
<AllowLocalProxyConnections>true</AllowLocalProxyConnections>
<AuthenticationTimeout>12</AuthenticationTimeout>
<AutoConnectOnStart UserControllable="true">false</AutoConnectOnStart>
<MinimizeOnConnect UserControllable="true">true</MinimizeOnConnect>
<LocalLanAccess UserControllable="true">false</LocalLanAccess>
<DisableCaptivePortalDetection UserControllable="true">false</DisableCaptivePortalDetection>
<ClearSmartcardPin UserControllable="true">true</ClearSmartcardPin>
<IPProtocolSupport>IPv4,IPv6</IPProtocolSupport>
<AutoReconnect UserControllable="false">true
<AutoReconnectBehavior UserControllable="false">ReconnectAfterResume</AutoReconnectBehavior>
</AutoReconnect>
<AutoUpdate UserControllable="false">true</AutoUpdate>
<RSASecurIDIntegration UserControllable="false">Automatic</RSASecurIDIntegration>
<WindowsLogonEnforcement>SingleLocalLogon</WindowsLogonEnforcement>
<WindowsVPNEstablishment>LocalUsersOnly</WindowsVPNEstablishment>
<AutomaticVPNPolicy>false</AutomaticVPNPolicy>
<PPPExclusion UserControllable="false">Disable
<PPPExclusionServerIP UserControllable="false"/>
</PPPExclusion>
<EnableScripting UserControllable="false">false</EnableScripting>
<EnableAutomaticServerSelection UserControllable="false">false
<AutoServerSelectionImprovement>20</AutoServerSelectionImprovement>
<AutoServerSelectionSuspendTime>4</AutoServerSelectionSuspendTime>
</EnableAutomaticServerSelection>
<RetainVpnOnLogoff>false
</RetainVpnOnLogoff>
<AllowManualHostInput>true</AllowManualHostInput>
</ClientInitialization>
<ServerList>
<HostEntry>
<HostName>VPN IOS-XE</HostName>
<HostAddress>vpn.example.com</HostAddress>
<PrimaryProtocol>IPsec
<StandardAuthenticationOnly>true
<AuthMethodDuringIKENegotiation>EAP-AnyConnect</AuthMethodDuringIKENegotiation>
</StandardAuthenticationOnly>
</PrimaryProtocol>
</HostEntry>
</ServerList>
</AnyConnectProfile>
更改<HostName>VPN IOS-XE</HostName>和<HostAddress>vpn.example.com</HostAddress>为自己的内容,然后将文件另存为acvpn.xml,并将其放置在C:\ProgramData\Cisco\Cisco AnyConnect Secure Mobility Client\Profile目录中。将该文件上传一份到路由器的flash中。
针对16.9之前的设备拨号,需要将BypassDownloader选项设置为true,例如:
<?xml version="1.0" encoding="UTF-8"?>
<AnyConnectLocalPolicy xmlns="http://schemas.xmlsoap/encoding/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://schemas.xmlsoap/encoding/ AnyConnectLocalPolicy.xsd" acversion="4.6.03049">
<BypassDownloader>true</BypassDownloader>
<EnableCRLCheck>false</EnableCRLCheck>
<ExcludeFirefoxNSSCertStore>false</ExcludeFirefoxNSSCertStore>
<ExcludeMacNativeCertStore>false</ExcludeMacNativeCertStore>
<ExcludePemFileCertStore>false</ExcludePemFileCertStore>
<ExcludeWinNativeCertStore>false</ExcludeWinNativeCertStore>
<FipsMode>false</FipsMode>
<RestrictPreferenceCaching>false</RestrictPreferenceCaching>
<RestrictTunnelProtocols>false</RestrictTunnelProtocols>
<RestrictWebLaunch>false</RestrictWebLaunch>
<StrictCertificateTrust>false</StrictCertificateTrust>
<UpdatePolicy>
<AllowComplianceModuleUpdatesFromAnyServer>true</AllowComplianceModuleUpdatesFromAnyServer>
<AllowISEProfileUpdatesFromAnyServer>true</AllowISEProfileUpdatesFromAnyServer>
<AllowServiceProfileUpdatesFromAnyServer>true</AllowServiceProfileUpdatesFromAnyServer>
<AllowSoftwareUpdatesFromAnyServer>true</AllowSoftwareUpdatesFromAnyServer>
<AllowVPNProfileUpdatesFromAnyServer>true</AllowVPNProfileUpdatesFromAnyServer>
</UpdatePolicy>
</AnyConnectLocalPolicy>该配置文件的位置在:
For Windows:
C:\ProgramData\Cisco\Cisco AnyConnect Secure Mobility Client\AnyConnectLocalPolicy.xml
For MAC OS:
/opt/cisco/anyconnect/AnyConnectLocalPolicy.xml
3,进行路由器的相关配置
aaa new-model
aaa authentication login acvpn-aaa-authen local
aaa authorization network acvpn-aaa-author local
username acvpn privilege 0 secret 9 $9$8BdJ39e86YA6/.$ETr4dZxCkZ5oAG25d3MneCLnjpUxhVU9RPQDQsLzFvA
#配置AAA的登录认证和授权策略,配置acvpn登录的本地用户名
crypto ikev2 authorization policy acvpn-ikev2-auth-policy
pool acvpn-ipv4-pool
def-domain iteachs.com
route set remote ipv4 192.168.0.0 255.255.0.0
#配置授权策略,包括IP地址,域名及远程授权的路由
crypto ikev2 proposal acvpn-ikev2-proposal
encryption aes-cbc-256
integrity sha256
group 15 19
crypto ikev2 policy acvpn-ikev2-policy
proposal acvpn-ikev2-proposal
#配置第一阶段策略
crypto ikev2 profile acvpn-ikev2-profile
match identity remote key-id *$AnyConnectClient$*
#anyconnect客户端的默认key-id为*$AnyConnectClient$*,可以在xml文件中进行自定义
authentication local rsa-sig
authentication remote anyconnect-eap aggregate
pki trustpoint acvpn.local
aaa authentication anyconnect-eap acvpn-aaa-authen
aaa authorization group anyconnect-eap list acvpn-aaa-author acvpn-ikev2-auth-policy
aaa authorization user anyconnect-eap cached
virtual-template 10
anyconnect profile acvpn
#15.8版本设备无法配置该命令
#配置acvpn的认证和授权策略
crypto vpn anyconnect profile acvpn bootflash:/acvpn.xml
#配置acvpn的对应的位置
crypto ipsec transform-set acvpn-ts esp-aes 256 esp-sha256-hmac
mode transport
#配置第二阶段策略
crypto ipsec profile acvpn-profile
set transform-set acvpn-ts
set ikev2-profile acvpn-ikev2-profile
#配置IPsec的profile
interface Virtual-Template10 type tunnel
description To:ACVPN-Client
ip unnumbered Dialer1
tunnel mode ipsec ipv4
tunnel protection ipsec profile acvpn-profile
#配置虚拟模板接口,并调用ipsec profile
ip local pool acvpn-ipv4-pool 192.168.51.1 192.168.51.1004,远程连接测试。
使用anyconnect拨号进行测试。
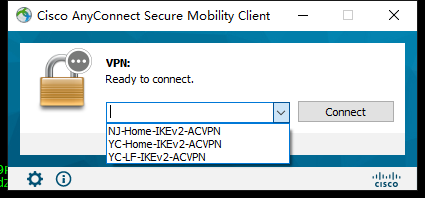
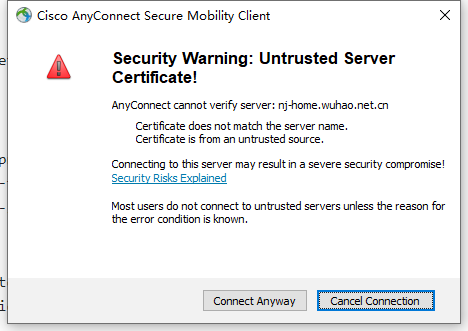
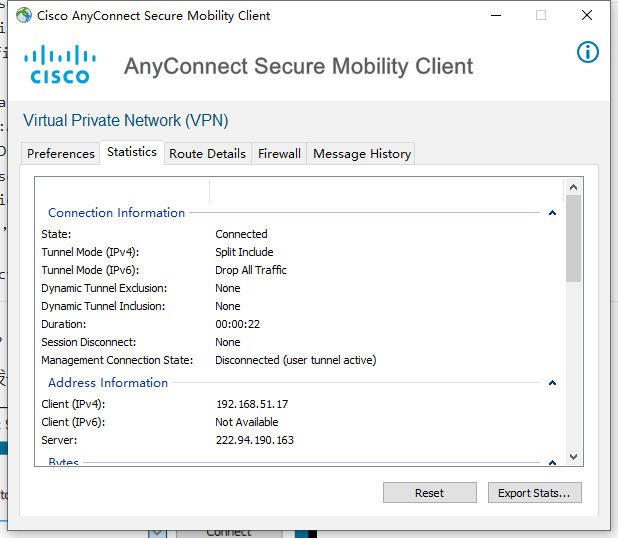
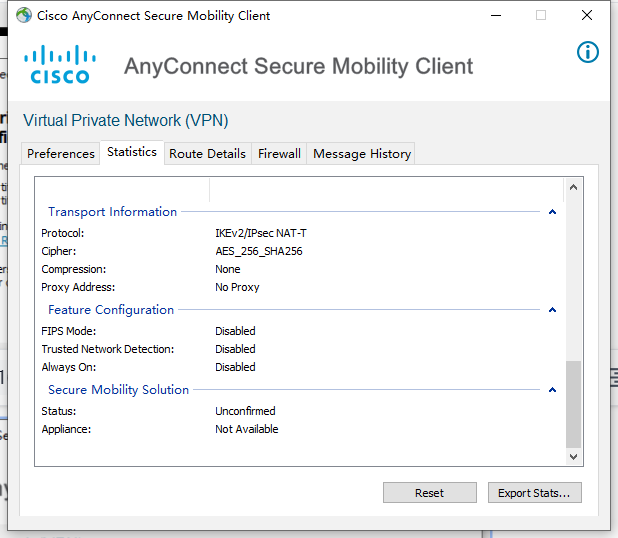
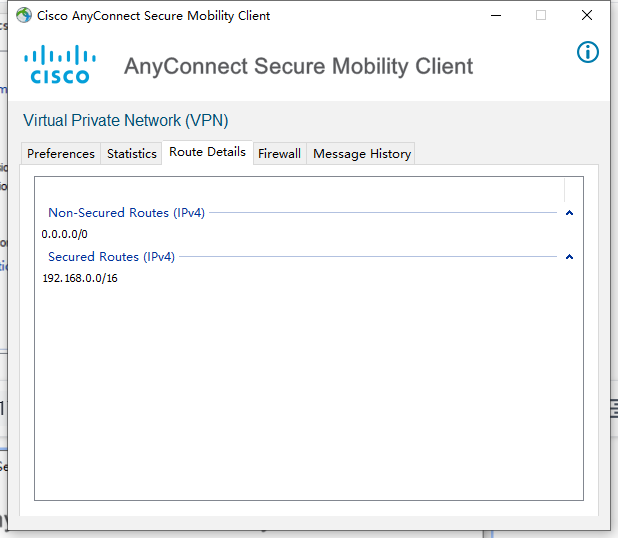
设备相关信息查看
#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
2 222.94.190.163/4500 192.168.50.18/53784 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA256, Hash: SHA256, DH Grp:19, Auth sign: RSA, Auth verify: AnyConnect-EAP
Life/Active Time: 86400/91 sec
IPv6 Crypto IKEv2 SA
#查看sa的状态
#show crypto ikev2 session detailed
IPv4 Crypto IKEv2 Session
Session-id:15, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote fvrf/ivrf Status
2 222.94.190.163/4500 192.168.50.18/53784 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA256, Hash: SHA256, DH Grp:19, Auth sign: RSA, Auth verify: AnyConnect-EAP
Life/Active Time: 86400/100 sec
CE id: 1038, Session-id: 15
Status Description: Negotiation done
Local spi: 75EF525E1AF0BC29 Remote spi: FCA0C4EDDFF11E9C
Local id: 222.94.190.163
Remote id: *$AnyConnectClient$*
Remote EAP id: acvpn
Local req msg id: 0 Remote req msg id: 9
Local next msg id: 0 Remote next msg id: 9
Local req queued: 0 Remote req queued: 9
Local window: 5 Remote window: 1
DPD configured for 0 seconds, retry 0
Fragmentation not configured.
Dynamic Route Update: disabled
Extended Authentication not configured.
NAT-T is detected outside
Cisco Trust Security SGT is disabled
Assigned host addr: 192.168.51.17
Initiator of SA : No
Child sa: local selector 0.0.0.0/0 - 255.255.255.255/65535
remote selector 192.168.51.17/0 - 192.168.51.17/65535
ESP spi in/out: 0x8E74BBA3/0xF9233843
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA256
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
IPv6 Crypto IKEv2 Session
#查看session的状态
至此操作完成。
相关参考连接:https://www.cisco.com/c/zh_cn/support/docs/security/flexvpn/200555-FlexVPN-AnyConnect-IKEv2-Remote-Access.html